Twitter is a popular social media app that allows users to communicate with their peers through short “tweets” or posts. Many users post whatever is on their mind, what happened to them during the day or to reach out to their friends. Twitter has the potential for cyberbullying, communicating with strangers, sharing fake news, and viewing inappropriate content. This GKIS Sensible Guide provides the information parents need to know to be familiar with Twitter and make informed decisions on when and how to allow their children to use Twitter.
What is Twitter?
Twitter is a social media platform that allows users to communicate with others using short messages. Twitter messages are called “tweets” and may include text, photos, and videos. Many people use Twitter to follow and reach out to others and to post tweets that aim at becoming “viral.”
Many companies like Target, Starbucks, and fast-food restaurants have Twitter accounts and use them to advertise their products and reach customers. Twitter is also useful for customer service and reporting issues to companies. During highly political times, it is not uncommon to see politicians and their followers using Twitter to garner support and attack opposing opinions.
Twitter has produced many popular influencers. Katy Perry and Justin Bieber are the popular influencers for entertainment/celebrity. Elon Musk, inventor of Tesla, and Jack Dorsey, founder of Twitter, are the top influencers in the technology area. There are several other areas with influencers including The Frugal Traveler as a travel influencer, Jamie Oliver as a health influencer, and Atelier Dore as a fashion influencer.[1]
How long has Twitter been around and how popular is it?
Twitter was founded by Jack Dorsey and officially launched in July of 2006. It is based in San Francisco and has over 25 offices around the world. In a statistic published in February 2020, 56.2% of United States Twitter users were male.[2] There is a wide age range of users with the most common ages 25 to 34 and 55 to 64.[3] In 2019, 330 million monthly active users were reported.[4]
How old is old enough for adoption?
According to Twitter’s Terms of Service, a user “must be at least 13 years old to use the Services.” [5] This age is selected for compliance with the U.S.’s Children’s Online Privacy Protection Act (COPPA). However, in Dr. Bennett’s book Screen Time in the Mean Time, she recommends no social media app adoption until at least the second semester of sixth grade, when kids have more social experience for creative problem solving and are no longer transitioning into middle school. (If the seventh grade is a transition year in your community, she recommends waiting until spring semester for the introduction). Because every child has unique strengths and vulnerabilities, parents are well suited to make the best-informed decision for their family.
What is included in the personal profile?
To create a Twitter account, you will need to enter your name, phone number or email, and create a password. The name you enter does not have to be your real name. It can also be a nickname. You will be directed to set a profile photo that will be used as a thumbnail for all your tweets. A cover photo may also be uploaded and will appear at the top of your profile.
A profile also includes your birthday, including the year, and the month and year that you joined Twitter. It also displays the number of people who follow you and the number of people that you follow. The profile also has four tabs that include Tweets, Tweets & replies, Media, and Likes.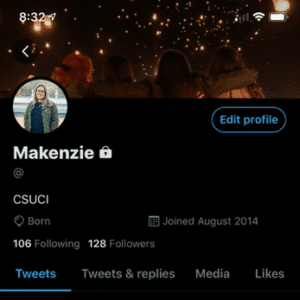
- Tweets: Shows all tweets the user has posted or retweeted.
- Tweets, retweets, & replies: Shows all tweets the user has posted or retweeted and any replies to tweets.
- Media: Shows any photos, videos, or gifs the user has tweeted.
- Likes: Shows all tweets the user has liked.
When clicking on a stranger’s profile, it will display if they are following you. It will also list everyone that follows them and that you follow. It also gives you an option to follow the user, turn on their notifications, send them a direct message, and mute, block, or report.
What are the privacy options?
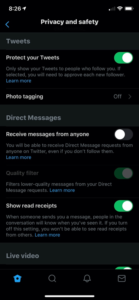
When clicking on “Privacy and Safety” in your settings, Twitter gives you several options which include information on protecting your tweets, direct messages, discoverability and contacts, safety, and personalization and data.
- Tweets
- The Protect your Tweets option allows users to only show their tweets to those that follow them. This also requires users to approve their followers.
- The location information option allows users to add their location to each of their tweets. Users also have the ability to delete all location information.
- The photo tagging option allows users to block others from tagging them in photos.
- Direct Messages
- Users are able to block others from messaging them
- Users are able to turn on or off their read receipts which notify the sender with the time they read their message.
- Discoverability and Contacts
- Users are able to allow people to find their accounts using their phone number or email address.
- Safety
- Users have the option of blocking media that may contain sensitive content
- User can also mark the media they tweet as containing sensitive content
- Users have the option of muting works or account
- Users can block accounts which means they will no longer see the account and the account will no longer see their account
- Users can change their notification settings or turn off notifications
- Personalization and Data
- Through these settings, users can control how Twitter personalizes content and collects and shares certain data
- Users can block Twitter from sharing their data with business partners.
What are the risks for use?
Inappropriate Content
It is easy for users to stumble upon potentially inappropriate content for their age and/or fake news. If one user retweets or shares something potentially inappropriate, all their followers will see that post. The best way to prevent your child from viewing inappropriate content on their Twitter feed is to go through their privacy settings and make sure to block inappropriate accounts. Requiring your child to get approval before the following accounts is another way to prevent inappropriate content. Please note, however, that once on Twitter it is impossible to filter out all inappropriate content.
Cyberbullying
Twitter carries a major risk for cyberbullying due to the anonymous nature of the platform. Twitter users may use a fake name and photo in order to remain anonymous and then send harmful messages or leave harmful comments on others’ tweets. The best way to prevent cyberbullying is to have the Twitter profile set on private and only approve people who are known by the user.
Sub tweeting is another common form of cyberbullying that is found on the platform. Sub tweeting means posting a tweet about someone without specifically naming that person. Most subtweets are harmful and are used as a way to attack a person without having an explicit connection to that person. Once again, even with best efforts, it’s impossible to block all cyberbully behaviors once on the Twitter platform.
Communicating with Strangers
Users who have a public profile are able to be contacted by any Twitter user. This means that strangers of any age can message a user and send them text or photos. Predators have the ability to send messages to young users. A private Twitter account is the best way to prevent contact with strangers.
Distractibility & Constant Access
Twitter produces a wide variety of content which makes it easy to keep scrolling for hours. Users often start looking at one tweet which leads to others of similar content. The cycle can go on for hours. Also, consider how comfortable you are having your child’s friends have constant screen access with your child. Social media fills one’s digital inbox constantly, all-the-time.
GetKidsInternetSafe rates Twitter as a yellow-light app due to the easy access to strangers, inappropriate content, and the potential for cyberbullying. Twitter tries to block inappropriate content from being posted, but there are millions of users who post multiple times a day. If you do opt to allow Twitter, be sure and get your child’s username and password and monitor posts.

Thank you to CSUCI intern Makenzie Stancliff for co-authoring this article. For more information on keeping your child safe on social media, check out the Get Kids Internet Safe Screen Safety Toolkit. Be sure to add Twitter on to the free GKIS Connected Family Agreement as a “not yet.”
I’m the mom psychologist who will help you GetKidsInternetSafe.
Onward to More Awesome Parenting,
Tracy S. Bennett, Ph.D.
Mom, Clinical Psychologist, CSUCI Adjunct Faculty
GetKidsInternetSafe.com
Works Cited
[1] Meet The Top Twitter Influencers by Topic. (2018, February 20). Retrieved from https://izea.com/2018/02/20/influencers-on-twitter/
[2] Clement, J. (2020, February 18). U.S. Twitter user distribution by gender 2020. Retrieved from https://www.statista.com/statistics/678794/united-states-twitter-gender-distribution/
[3] Clement, J. (2019, August 9). Twitter: U.S. user age distribution 2018. Retrieved from https://www.statista.com/statistics/192703/age-distribution-of-users-on-twitter-in-the-united-states/
[4] Clement, J. (2019, August 14). Twitter: number of active users 2010-2019. Retrieved from https://www.statista.com/statistics/282087/number-of-monthly-active-twitter-users/
[5] Twitter Terms of Service. (n.d.). Retrieved from https://twitter.com/en/tos
Photo Credits
Photo by Sara Kurfeß on Unsplash