The pandemic of 2020 has many of us working from home. For most of us, our internet must work quickly and efficiently to stay productive. The increasing demand for having reliable, quick internet coupled with new technology compatible with the internet has led to the creation of 5G, a new wireless internet connection. But many feel anxious about this new mobile network, wondering what impacts it may have on our health, privacy, and security. Learn all about 5G in today’s GKIS article.
What is 5G?
Introduced in 2019, 5G is the latest form of wireless internet connection. 5G will enhance internet connections and download speeds using “millimeter waves.” These waves are smaller and move faster than previously used 4G waves, allowing the space needed for the Internet of Things (IoT).
What is “IoT”?
IoT stands for the Internet of Things, which refers to wired and WiFi-connected home products that collect data about our daily behaviors. This data is then used to better target us for marketing, to improve services, and to make more efficient, informed decisions based on probability and statistics. Currently, we have 6.5 billion devices connected to the internet. It is estimated that by 2026, more than 75 billion devices will be connected to the internet generating $1.1 trillion a year.1
How will IoT be applied?
Consumer
Door locks, security cameras and monitors, home appliances, light fixtures, thermostats, smart televisions, smart refrigerators, media platforms, and voice-assisted digital assistants like Amazon’s Alexa, Apple’s Siri, Google’s Google Assistant, and Microsoft’s Cortana will have the capacity to sense, analyze, and act as well as deliver data to the corporation for analysis, storage, and sharing.
Commercial

Military
Drones, robots, surveillance, and wearable biometrics are being implemented for warfare.
Industrial

Infrastructure
Barcelona has embraced the development of becoming a “smart city” through the use of IoT. The results appear to have a positive impact on their economy, resulting in a $50 million per year revenue on smart parking alone. They have decreased their costs in energy consumption by $37 million a year using self-regulating lights, as well as saving $58 million a year with “smart gardens” that water plants at the right place and the right time.5
Security, Privacy, and the Internet of Things
We are headed for a paradigm shift, where our physical belongings are increasingly becoming computer systems. What was first “internet security” will be “everything security.” Unfortunately, most IoT software being manufactured and marketed is poorly written, insecure, and in the hands of corporations. Although you may trust the corporation with your data, do you trust the hackers who can breach that corporation’s controls to get access to it?
Security just isn’t a pressing concern for corporations and consumers. As consumers, we want inexpensive devices that work. Having insecure appliances connected to the internet like a thermometer, which is normally intended to last a long time, is dangerously allowing hackers the opportunity of exploitation.6 You might be able to get away with leaving the front door of your home unlocked, but in the cyberworld, every door can be attacked. Security professionals and hackers alike use what is known as wardriving to locate and record WiFi networks using a GPS.7
Wardriving is a GPS used to locate vulnerable and unprotected WiFi from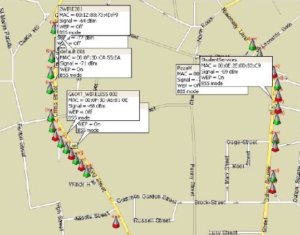

I’m the mom psychologist who will help you GetKidsInternetSafe.
Onward to More Awesome Parenting,
Tracy S. Bennett, Ph.D.
Mom, Clinical Psychologist, CSUCI Adjunct Faculty
GetKidsInternetSafe.com
Work Cited
1 Securitytoday.com The IoT Rundown for 2020 Stats, Risks, and Solutions
2 Cnet.com 5G is still a little magic, a little smoke and mirrors
3 Career.du.edu University Denver How will the Internet of Things Affect your Job Prospects
4 Digital Trends Leafy greens are grown by machines at new, automated Silicon Valley farm
5 Datasmart.ash.harvard.edu
6 Nist.gov What is the Internet of Things (IoT) and How can we secure it?
7 Techterms.com Wardriving
8 Internet of Things Security Ken Munro
9 Finance-monthly.com The Worst and Weirdest IoT Hacks of All TImes
10 Techrepublic.com Who has banned Zoom? Google, NASA, and more
Photo Credits
Flickr- by 4timesfasttechnologies
Flickr- by Jefferson William
Flickr- by terrasphere
Flickr- by Rick Teremi
Flickr- by Mike Dent